 One of the first and most important things to configure on any Cisco device after allowing telnet or SSH, is to restrict who is allowed to access the device. Of course having a password on the lines is the first step and often configured correctly. The unfortunate thing about password security, especially when discussing telnet, is that telnet sends all traffic in clear text. This means that if someone was to sniff the line while you logged onto a router using a telnet session, they would be able to see your password and hence gain access to the device.
One of the first and most important things to configure on any Cisco device after allowing telnet or SSH, is to restrict who is allowed to access the device. Of course having a password on the lines is the first step and often configured correctly. The unfortunate thing about password security, especially when discussing telnet, is that telnet sends all traffic in clear text. This means that if someone was to sniff the line while you logged onto a router using a telnet session, they would be able to see your password and hence gain access to the device.
As an additional method for securing your Cisco devices, it’s a good idea to bind an ACL (Access Control List) to the VTY’s (Virtual Terminal Lines). This will only allow IP addresses included in the ACL to create a connection to the device in addition to needing the password for the lines.
If we look at the diagram below, I might want to restrict telnet access into R1 so telnet will only be allowed to take place from AOIP.ORG and not from any other device or computer.
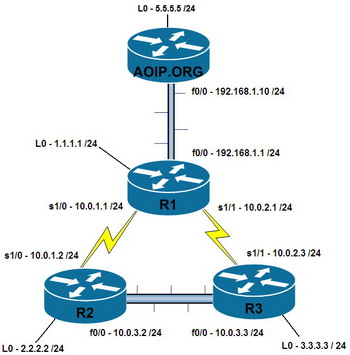
In order to achieve the above, the following commands would need to be configured.
R1# conf t
Enter global configuration mode
R1(config)# access-list 1 permit host 192.168.1.10 log
This creates a standard access-list and logs the amount of times this access-list is matched. No deny statement is needed as there is always an implicit deny any statement at the end of every access-list
R1(config)# line vty 0 4
Enter the Virtual lines
R1(config-line)# access-class 1 in
Attach the access-list to the virtual lines for traffic inbound TO the router.
Below is the live demo.





